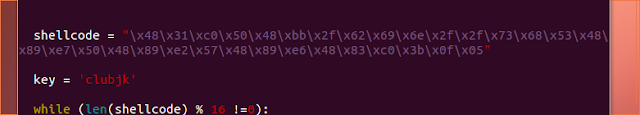
When malware becomes optional and speed becomes the weapon of choice
The Numbers That Should Wake You Up
CrowdStrike's 2026 Global Threat Report dropped last week, and the statistics are sobering. We're not looking at incremental change—we're looking at a fundamental shift in how attackers operate.
The headline figures:
- 89% increase in attacks by AI-enabled adversaries
- 82% of detections in 2025 were malware-free
- 29 minutes average breakout time (down 65% from 2024)
- 27 seconds—the fastest observed breakout
Let that last number sink in. Twenty-seven seconds from initial access to lateral movement. That's not enough time to finish a sip of coffee, let alone mount an effective response.
The Rise of the "Evasive Adversary"
What CrowdStrike calls the "evasive adversary" represents a new breed of threat actor—one that doesn't need to drop malware to achieve their objectives. Instead, they're "living off the land," using legitimate tools and native system capabilities to blend into normal operations.
This isn't new in concept. PowerShell-based attacks and LOLBins (Living Off the Land Binaries) have been around for years. What's changed is the scale and sophistication that AI enables.
How AI Changes the Game
1. Automated Reconnaissance at Scale
Traditional attackers might spend days or weeks mapping a network. AI-enabled adversaries can analyze network topology, identify high-value targets, and map privilege escalation paths in minutes. The reconnaissance phase that once took a human team weeks now happens in the time it takes to brew coffee.
2. Adaptive Evasion Techniques
Machine learning models can analyze defensive patterns in real-time and adjust tactics accordingly. If one approach triggers an alert, the AI pivots instantly—testing variations until it finds a path that works. It's like playing chess against an opponent who can simulate a million moves per second.
3. Hyper-Personalized Social Engineering
AI-generated phishing has moved beyond clumsy grammar errors and generic templates. Today's AI can scrape social media, analyze communication patterns, and craft messages that mimic the writing style of colleagues, executives, or trusted vendors. The Nigerian prince has been replaced by a convincing facsimile of your CFO.
4. Malware-Free Persistence
Why drop a payload when you can use the tools already installed? AI agents can identify and abuse legitimate remote access tools, cloud services, and administrative utilities. The activity looks normal because it is normal—just weaponized.
Why Traditional Defenses Are Failing
The cybersecurity industry has spent decades building defenses around a simple model: detect the malware, block the malware, analyze the malware. But when 82% of attacks don't use malware, that model breaks down.
The Signature Problem
Signature-based detection—whether for files, network traffic, or behaviors—relies on knowing what to look for. AI-enabled adversaries generate unique approaches for each target. By the time a signature exists, the attack has already succeeded.
The Speed Gap
The average SOC takes 197 days to identify a breach. AI-enabled adversaries achieve their objectives in under 30 minutes. We're not just behind—we're operating in different time zones.
The Alert Fatigue Trap
Security teams are drowning in false positives. When everything generates an alert, analysts become desensitized. AI-enabled attackers exploit this by crafting attacks that generate just enough noise to blend in, but not enough to trigger immediate escalation.
Building a Defense for the AI Era
If we can't out-speed the attackers, we need to out-smart them. Here's what effective defense looks like in 2026:
1. Behavioral Detection Over Signature Matching
Stop looking for malware and start looking for anomalies. Baseline normal behavior for users, systems, and networks. When someone accesses resources they've never touched, at unusual times, from unexpected locations—that's your signal.
Key capabilities:
- User and Entity Behavior Analytics (UEBA)
- Network traffic analysis with ML-powered anomaly detection
- Privileged access monitoring with context-aware alerting
2. Assume Breach, Detect Fast
The 27-second breakout tells us that prevention alone is insufficient. Design your architecture assuming compromise will happen. Focus on:
- Micro-segmentation: Limit lateral movement opportunities
- Zero Trust: Verify every access request, every time
- Deception technology: Honeypots and honeytokens that trigger high-fidelity alerts
3. Automate the Response
If attackers use AI for speed, defenders must match it. Manual incident response processes that take hours or days are no longer viable.
Automated response capabilities:
- Isolate compromised endpoints within seconds
- Revoke sessions and credentials automatically
- Dynamic firewall rules based on threat intelligence
- SOAR playbooks for common attack patterns
4. Threat Hunting, Not Just Monitoring
Passive monitoring waits for alerts. Threat hunting proactively searches for indicators of compromise that evaded detection.
Hunting hypotheses to explore:
- Users accessing cloud resources outside business hours
- Administrative tools executed by non-admin accounts
- Unusual data transfer volumes to external destinations
- PowerShell execution with encoded commands
5. Adversarial AI for Defense
Fight fire with fire. Deploy AI systems that:
- Generate synthetic attack scenarios for testing defenses
- Predict attacker paths based on network topology
- Automatically correlate disparate events into attack chains
- Continuously adapt detection models based on new threat intelligence
The Human Element
Technology alone won't save us. The most critical defense is a well-trained team that understands:
- What AI-enabled attacks look like in practice
- How to investigate without relying on malware signatures
- When to escalate based on behavioral indicators
- How to respond under time pressure
Invest in continuous training. Run tabletop exercises with realistic scenarios. Build muscle memory for the 27-second reality.
Looking Ahead
The 89% increase in AI-enabled attacks isn't a spike—it's the new baseline. As AI tools become more accessible and sophisticated, the barrier to entry for advanced attacks continues to drop.
We're entering an era where the question isn't "if" you'll face an AI-enabled adversary, but "when." And when that moment comes, you'll have 29 minutes—or less—to respond.
The defenders who thrive in this environment won't be the ones with the most tools or the biggest budgets. They'll be the ones who adapted their thinking, their processes, and their technology to match a threat that moves at machine speed.
The 27-second breakout is a wake-up call. The question is: are you listening?
Resources for Deeper Dive
John Kennedy is a cybersecurity professional with 34 years of military experience in information warfare and 9 years in civilian penetration testing and security assessment. He writes about the intersection of AI, cloud security, and modern threat landscapes.